Domain Control Validation (aka DV or Domain Validation) Overview
In order to establish ownership or authorization to acquire an SSL Certificate for a specific domain, proof of control over the domain must be established.
Domain Control Validation (DCV) can be established by the following methods:
All SSL/TLS certificates, including DV (Domain Validated), OV (Organization Validated), and EV (Extended Validation) Certificates require one of these validation methods to be performed successfully before issuance.
For UCC (also known as SAN or Subject Alternative Name) SSL/TLS certificates, domain validation must be performed on each domain included, using any method listed above (or a combination of these methods).
On a UCC order, all domains listed must have a validation method selected and the validate button needs to be clicked in order to start the domain validation process.
If trying to validate a domain that doesn’t respond publicly, temporarily redirect to one that does with http/http file upload or use cname validation.
You can read more about SSL.com’s validation requirements here.
Email Challenge Response
Upon order placement, an email is sent to an authorized email address selected during the order process. Contained within this email is a link the the recipient of the email can follow and enter in a validation code found in the email. Once this process is completed, domain control has been established.
The accepted list of email addresses for a domain that SSL.com is authorized to send the DCV email to is as follows:
- webmaster@
- hostmaster@
- postmaster@
- administrator@
- admin@
- Domain contacts (domain name registrant, technical contact, or administrative contact) listed in the base domain’s WHOIS record. This option will be deprecated by SSL.com on December 2, 2024. Please refer to this article for more detailed information: SSL.com to Deprecate Domain Contact-Based Email Domain Control Validation on December 2, 2024
There are also options to validate any of the above acceptable email addresses through DNS CAA and DNS TXT. For these two options, the DNS records must be properly configured as follows:
- DNS CAA Record Example (TTL may vary):
exampledomain.com. 3600 CAA 0 contactemail “hostmaster@exampledomain.com“ - DNS TXT Record Example (TTL may vary):
_validation-contactemail.exampledomain.com 3600 TXT “hostmaster@exampledomain.com“
File lookup over HTTP/HTTPS
This method requires placing a file on the website that is to be protected.
The file is created from taking two hashes of the Certificate Signing Request (CSR) and uploading a text file with that information to a specific location on the server. The file has the MD5 hash for a name with the SHA-256 hash as the first line of the contents of the file. The next line of the file has the term “ssl.com”, while the last line of the file has a unique token. All actual hash and random values will be presented to you via the user portal.
For instance, for a new CSR is created for the domain name www.yoursite.tld, where the MD5 hash of the CSR is:
8593532A8FA01E6CEBB0B7E85E510D0F
the SHA-256 hash for the CSR is:
c9c863405fe7675a3988b97664ea6baf442019e4e52fa335f406f7c5f26cf14f
and the unique token for the order is:
10TmfZdb9tj
Then the DCV file would be named 8593532A8FA01E6CEBB0B7E85E510D0F.txt and would have the contents:
c9c863405fe7675a3988b97664ea6baf442019e4e52fa335f406f7c5f26cf14f ssl.com 10TmfZdb9tj
The file must be accessible at via HTTP on port 80, or via HTTPS on port 443. SSL.com will check for the existence of this file to satisfy domain control validation. The file cannot be altered in any way or reached via redirection or other .htaccess directives. The file must be placed in the .well-known/pki-validation/ folder on your domain. You will need to create this folder.
In this example, the DCV file should be placed here:
http://www.yoursite.tld/.well-known/pki-validation/8593532A8FA01E6CEBB0B7E85E510D0F.txt
After an order is successfully placed, SSL.com’s automated server will start looking for this file at the above location. When it is able to see the file, domain control validation will be satisfied.
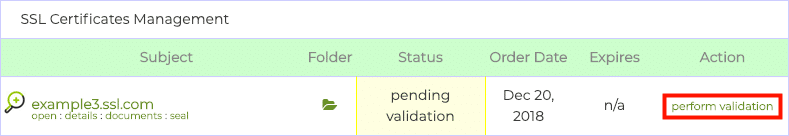
To download the DCV file, first click the Perform Validation link, located in the Action column of the Orders tab to open the Domain Validation page.
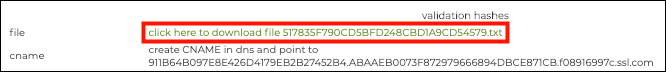
The file is downloadable under validation hashes.
DNS CNAME lookup for domain
This method requires you to create a CNAME entry in your domain’s DNS record that is pointed at ssl.com (and in some cases comodoca for Comodo chained certificates). An MD5 hash as well as a SHA-256 hash of the CSR are required for this CNAME entry, plus a unique token.
All of these values are available from the Domain Validation page in your user portal. First, click the Perform Validation link, located in the Action column of the Orders tab to open the Domain Validation page.
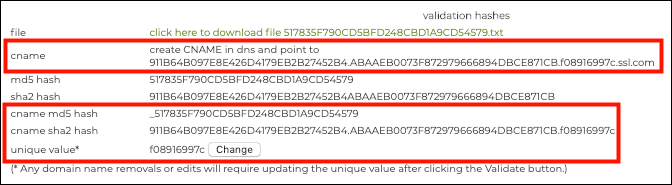
All of the information needed to create the CNAME entry is available under validation hashes.
The CNAME entry should follow this formula:
_<MD5 hash>.<domain> <TTL> IN CNAME <SHA-256 hash>.<unique token>.ssl.com
Please notice the underscore at the beginning of the entry, which is required. Additionally, because the SHA-256 hash is 64 characters long, it will need to be split into two 32-character subdomains. Therefore, the completed DNS record will look like this:
_517835F790CD5BFD248CBD1A9CD54579.yoursite.tld. 14400 IN CNAME 911b64b097e8e42d4179eb2b27452b4.abaaeb0073f872979666894dbce871cb.f08916997c.ssl.com
All actual hash and random values will be presented to you via the user portal.